


In light of the incident on dYdX v3 involving large SUSHI and YFI price movements, we want to provide the community with a breakdown of these activities. While no user funds were compromised, these price movements appear to be an oracle manipulation attack and dYdX Trading Inc. is exploring legal remedies against the attacker. Here is what we understand about the attacker’s action on dYdX v3, as well as our learnings as to how to prevent such incident going forward. All of this is based on currently available information and assessment, which may adjust as we learn more.
Efforts to Trace the Attacker & Collaborate with Law Enforcement
Thanks to the efforts of our team, partners in the community and forensics contractors, investigative results have uncovered the identity of the attacker and we are in contact with them. We may provide further updates with relevant developments.
dYdX is assisting law enforcement in their investigation of this matter and is assessing all legal options. dYdX is committed to taking any legal action it deems appropriate in these circumstances.
Next steps on dYdX v3:
We have implemented updates to risk controls on dYdX v3, including:
Revised margining in less-liquid markets
Initial margin fraction will adjust automatically when abnormal activity occurs, which affects the ability to withdraw unrealized profit but not liquidation prices.
Improved open-interest monitoring and alerting, especially over long time frames
Together, these measures will impede other bad actors from trying to use the same strategy to take levered positions, manipulate spot prices, withdraw against mark to market gains, and repeat. Additionally, we have strengthened our relationships with blockchain forensic investigation experts who are assisting us with identifying bad actors on-chain prior to manipulative behavior, as well as after the occurrence of manipulative behavior.
Next steps on the dYdX Chain:
The default code of the v4 open-source software (the ”dYdX Chain”) is already designed with these risks in mind in several ways.
1. Redesigned liquidation engine: For the dYdX Chain, we rebuilt the liquidation engine from the ground up. It is designed to detect liquidatable positions, liquidate them intelligently, and falls back to automatic deleveraging (ADL) when necessary. Just like in dYdX v3, any deployer of dYdX Chain could use an insurance fund as the first line of defense in the rare cases that positions cannot be liquidated before an account’s margin is exhausted
In the event that an insurance fund is unable to cover a position’s liquidation, the dYdX Chain automatically closes the position against an offsetting position, in a process called automatic deleveraging (ADL).
As we continue to develop the dYdX Chain software, we are aiming to ensure that only accounts which hold a position in an instrument are exposed to risk from its price fluctuations, and conversely that uninvolved accounts are totally insulated. This is in contrast to systems where failed liquidations may result in socialized losses across accounts regardless of their positions.
2. Data-driven market availability: We recommend that any deployers of dYdX Chain use data about market depth and trading activity across reference venues to determine (a) which underlying instruments to list perpetuals on and (b) the appropriate leverage to extend.
3. Variable margin fraction: We are introducing a new software feature which varies the initial margin fraction automatically if there are unusually large price movements. The intensity of this effect depends on the risk tier of the market and the degree of the price move.
Note that initial margin fraction only affects the ability for traders to take additional leverage by opening new positions or withdrawing collateral against their existing positions, and cannot change a trader’s liquidation price.
One reason the YFI attacker was able to build up leverage is that they were able to cycle deposits and withdrawals: first deposit to dYdX v3 and go long at max leverage, then push the spot price up, withdraw the mark to market gains from the long position, deposit using a new wallet address, and repeat. This variable margin fraction would have cut this cycle short, because the new initial margin fraction would have prevented withdrawals.
This feature will be available as part of the dYdX Chain as soon as next month.
4. New risk management tools: Finally, we are adding a suite of risk monitors in the software with a longer time horizon that will be difficult to manipulate, and we are actively researching additional measures to discourage manipulation, such as varying funding or margin fraction with OI or leverage buildup.
Timeline
The SUSHI Market Incident (10/29/23 - 11/3/23)
10/29/23 - 11/3/23: The attacker connected to dYdX v3 with over 100 wallet addresses (”accounts”), depositing approximately $5.3 million. They primarily took leveraged (5x) long positions in SUSHI-USD.
Spot Price Surge: Shortly after the attacker began building long positions, addresses linked to the attacker likely commenced buying $SUSHI across multiple venues. The price of $SUSHI soared by 180%, from about $0.67 to $1.20 between 10/31/23 and 11/3/23. The attacker continually withdrew unrealized profits from their long positions on dYdX and opened more long positions using new wallet addresses.
Margin Increase (11/1/23): To prevent the attacker from withdrawing their unrealized profits, the initial margin requirement for SUSHI-USD trades was raised to 100%.
Withdrawal of Profits (11/3/23): Once SUSHI’s price stabilized and market activities returned to normal the margin requirement was lowered back to 25%. Subsequently the attacker withdrew $5 million in profits after closing their positions.
Price Stabilization: Post-incident, SUSHI’s price remained over $1. The attacker appeared to have closed almost all of their long positions on dYdX v3.
The YFI Market Action (11/1/23 - 11/17/23)
11/1/23 - 11/10/23: Using around $10 million (including profits from the $SUSHI incident), the attacker targeted the YFI-USD market, again, with 5x leveraged long positions.
Open Interest Surge: During this time period, the open interest in the YFI-USD market on dYdX v3 spiked from $0.8 million to $67 million.
Spot Price Increase: From 11/9/23 to 11/17/23, $YFI ’s price jumped approximately 215%, going from around $6500 to over $14000. Throughout the period of the attack, addresses linked to the attacker likely bought YFI across multiple venues.
Continuous Profit Withdrawal: The attacker repeated their strategy of withdrawing unrealized profits and opening new positions.
Market Parameters Adjustment (11/17/23): The YFI-USD market’s initial margin requirement was increased, and the base position and incremental position size were decreased in order to limit the attacker's ability to withdraw further profits.
The YFI Crash (11/18/23)
Price Crash (11/18/23, 5AM UTC): $YFI ’s price plummeted nearly 30% in an hour.
Unsuccessful Position Closure: The attacker tried but largely failed to close their positions before the crash, managing to close only a small percentage.
Lack of Liquidity and Liquidation: With no liquidity available, most of the attacker’s remaining positions were liquidated only after the oracle price fell below their bankruptcy price.
Negative Equity: The attacker’s accounts ended up in negative equity, which automatically triggered deployment of the insurance fund to cover losses.
Please refer to Status Updates for a comprehensive coverage of parameter updates.
In-Depth Analysis of the Incident
On 11/1/23, we became aware of a large number of wallets that had opened highly leveraged SUSHI long positions, all linked to a single funding source. Upon investigation, we confirmed 132 addresses that had connected with dYdX v3 tied to this funding source, involving ETH and USDC transfers. For instance, this address received ETH from the root address and deposited 22,000 USDC to a wallet address connected to dYdX v3.
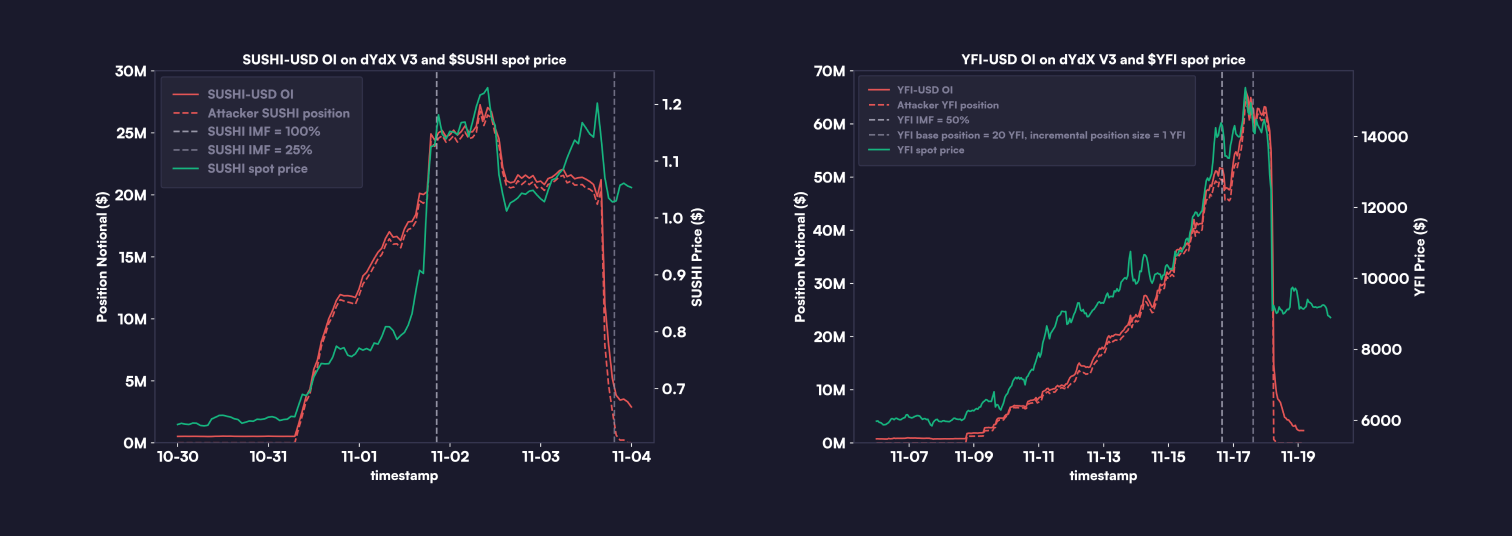
During this period, we noticed a significant increase in open interest in the SUSHI-USDC market, coinciding with a rise in SUSHI's price. Recognizing this activity as a potential market manipulation by a single attacker, we raised the initial margin requirement to 100%, aiming to prevent further profitable withdrawals from these trades. Once SUSHI's price stabilized, and market activities returned to normal, the margin requirement was adjusted back.
A few days later, a similar trading pattern emerged in the YFI-USDC market. Market parameters were promptly adjusted, including initial margin, base position and incremental position size, to curb the attacker’s ability to withdraw profits.
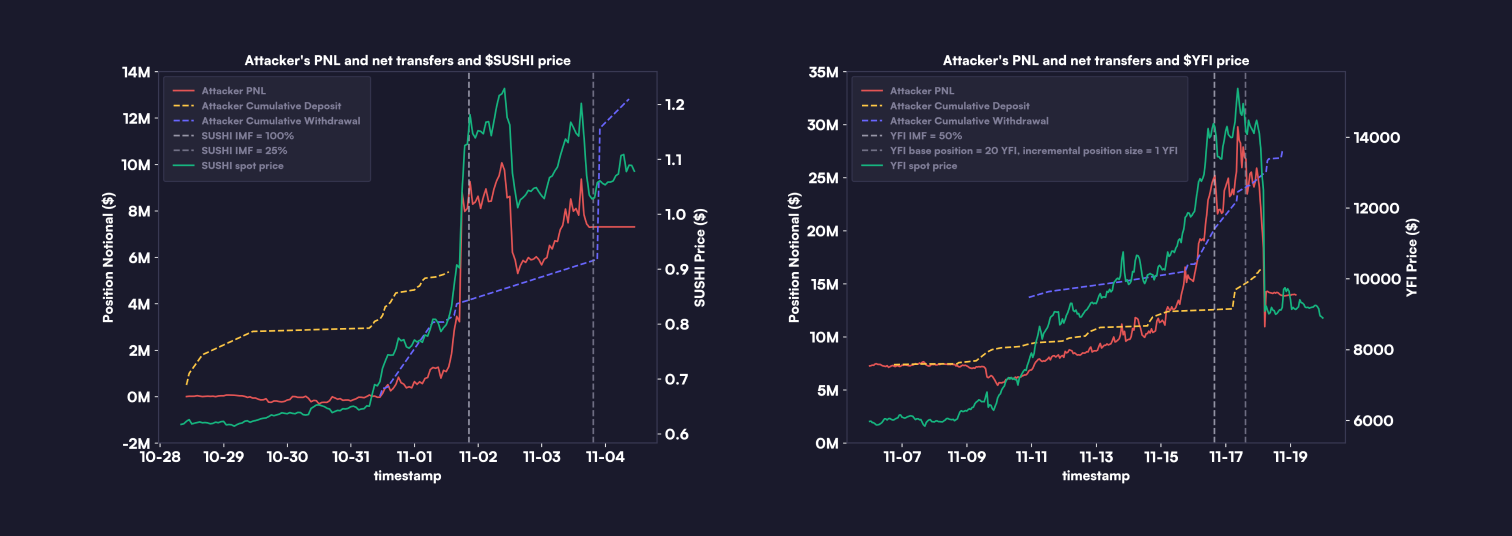
The attacker appeared to have a clear strategy: build leveraged long positions on dYdX v3 prior to purchasing
$SUSHI
and
$YFI
spot. Ultimately the price moves in
$SUSHI
and
$YFI
were possibly due to some combination of an organic price move and the attacker’s coordinated aggressive buying in spot markets. Early in the price surges, the attacker withdrew unrealized profits from their long positions, connected new wallet addresses to dYdX v3, and redeposited these profits to expand their long positions. This was possible because the unrealized profits counted as account equity in margin calculations. In other words, for a given account, the attacker could withdraw up to account equity - IMF * position size where account equity = USDC collateral deposited + unrealized profit.
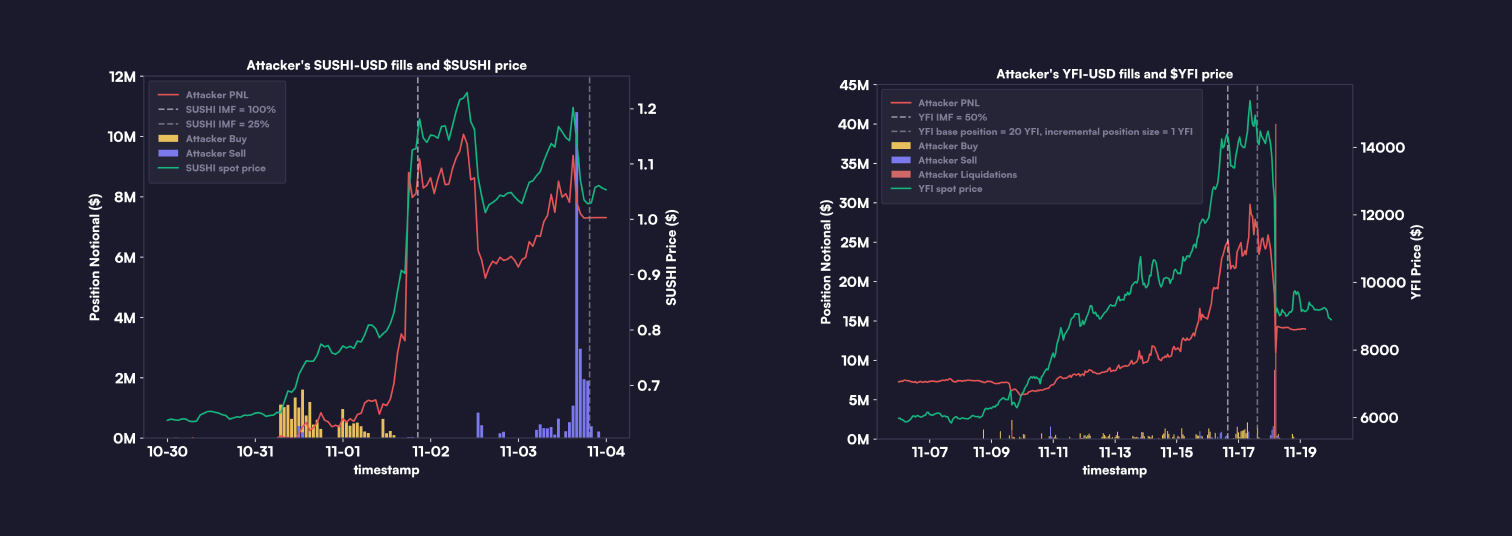
A notable difference between the $SUSHI and $YFI incidents was the aftermath of the price surge. While $SUSHI maintained its value above $1 even after a decline in open interest, $YFI experienced a significant price crash leading to a major liquidation event. During this drop, the liquidity on dYdX v3 was severely affected, making it impossible to liquidate the attacker’s large YFI long positions before they fell into negative equity. Consequently, the insurance fund automatically covered the losses incurred from these liquidations.
Our analysis suggests that the attacker likely did not profit on dYdX v3 from the price crash of $YFI . Examination of short positions in the market prior to liquidations indicates a natural distribution, with no apparent link to the attacker. Furthermore, the timing of the opening of these short positions do not align with the attacker's strategy, making it improbable that the attacker held significant short positions using unidentified wallet addresses.
In total, the attacker managed to withdraw approximately $27 million from dYdX v3, having initially deposited around $16 million. The attacker’s trading activities led to a more than $9 million drain from the insurance fund.
Terms and Conditions
dYdX Trading Inc. (”dYdX”) does not deploy or run the dYdX Chain for public use, or operate or control any dYdX Chain infrastructure. This document contains information about certain default settings of the dYdX Chain, or non-mandatory guidelines and suggestions that may help with using the dYdX Chain. dYdX is not responsible for any actions taken by other third parties who use the dYdX Chain or other open source software. dYdX services and products are not available to persons or entities who reside in, are located in, are incorporated in, or have registered offices in the United States or Canada, or Restricted Persons (as defined in the dYdX Terms of Use). The content provided herein does not constitute, and should not be considered, or relied upon as, financial advice, legal advice, tax advice, investment advice or advice of any other nature, and by you agree that you are responsible to engage advisors related to the foregoing content. The information contained herein, and any use of the dYdX Chain, are subject to the Terms of Use and v4 Terms of Use.